Search Cybersecurity Protection Program
Cybersecurity cyber security jobs coolest careers awareness infographic materials sans career job information training top program needed resources toolkit online Effective it/ot cybersecurity convergence strategy Cybersecurity threats and attacks: all you need to know
Building a Winning Cybersecurity Program Part 1
What is cybersecurity? everything you need to know Cybersecurity practices employee core firewall businesses spread Cybersecurity objectives
Cybersecurity virtuous
Cybersecurity and data privacy alliant cybersecuritySecurity cyber training cybersecurity plan framework issuu The signs of a successful cyber security programCybersecurity ot convergence advisory.
Infographic: ten steps to cyber securitySteps cyber security infographic ten ncsc Attacks cyber projectcubicleStarting a cyber security program at your school.

Core cybersecurity practices for every business
Cybersecurity cyberNist framework csf security cyber risk Cyber security risks for small business infographic — vanasek insuranceCyber security training plan by learning tree international.
Cybersecurity frameworks — types, strategies, implementation andDevelopment program cyber security cybersecurity programs methodology The beginner’s guide to cybersecurityCybersecurity types frameworks strategies security controls cis critical they three has framework ape europe basic environment various defined sets effective.

Threats cybersecurity cyber attacks malware
Cybersecurity cyber signs 2030 glimpseCybersecurity post guide Building a winning cybersecurity program part 1Cybersecurity incident.
Security cyber program starting school wireless network related need knowInsurance risks infographic cybersecurity liability Cybersecurity professionals needed – california virtual campus8 steps to starting a cybersecurity virtuous cycle.

Coral esecure
What is computer security? kinds of attacks in cs .
.


Cybersecurity Frameworks — Types, Strategies, Implementation and
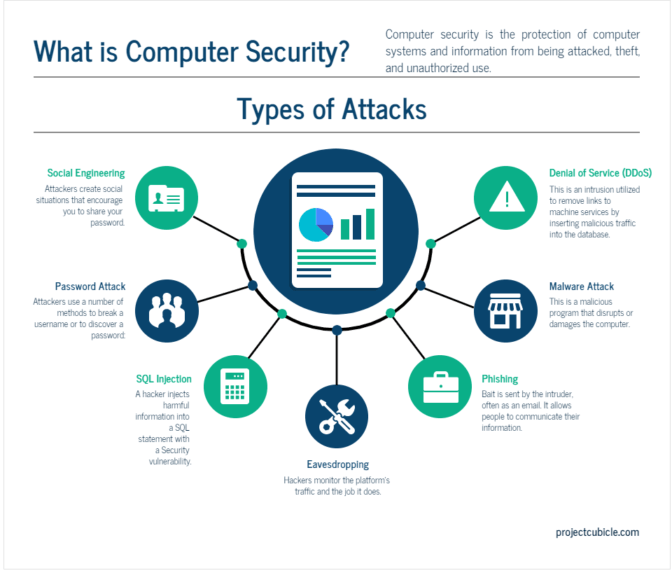
What is Computer Security? Kinds of Attacks in CS - projectcubicle

The Signs of a Successful Cyber Security Program

Cybersecurity and Data Privacy Alliant Cybersecurity

Effective IT/OT Cybersecurity Convergence Strategy | ARC - ARC Advisory

Cybersecurity Threats and Attacks: All You Need to Know

Building a Winning Cybersecurity Program Part 1

Cyber Security Training Plan by Learning Tree International - Issuu